Submitted by: Kate Esprit & Meghan Jacquot
Overview: LAPSUS$ Group
What does Microsoft, Samsung, T-Mobile, Okta, and the Brazilian Ministry of Health all have in common? All of these entities have fallen victim to cyberattacks by the LAPSUS$ hacking group. LAPSUS$ Group is an international hacking and extortion group that mainly comprises teenage members. The group heavily relies on the use of the social media platform Telegram and has used it to boast publicly about their achievements in a way that teenagers often express joy over big accomplishments. Members of LAPSUS$ seem to give little care about the group’s operational security, as many of them have doxxed (publicly released personal information) each other out of mere annoyance.
Despite their relative immaturity, LAPSUS$ has successfully managed to exfiltrate data from large companies through social engineering, exploiting software vulnerabilities, and purchasing stolen credentials on underground forums such as Genesis Store.
The Rise of LAPSUS$
LAPSUS$ Group first became subject to widespread media attention in December 2021, when they launched a ransomware attack against the Brazilian Ministry of Health (Ministério da Saúde). The attackers compromised several of the health ministry’s systems, exfiltrating internal vaccination data and ordering officials to contact LAPSUS$ in order to retrieve the stolen information.

It quickly became apparent that members of LAPSUS$ were just getting started. Following the attack in Brazil, the group executed additional cyberattacks against at least 8 major technology companies. With each campaign, the group’s members utilized Telegram to dump stolen data and recruit additional members. In just a few short months, LAPSUS$ had acquired 50,000 subscribers on their Telegram channel and leaked at least hundreds of gigabytes of sensitive information.

The Fall of LAPSUS$
However, the LAPSUS$ chapter closed almost as quickly as the group’s rise to prominence. In March 2022, the City of London Police arrested 7 suspected members of LAPSUS$. One of the most surprising revelations to arise from these arrests was that the hackers were between ages 16 and 21. This means that some of the world’s most powerful technology companies were digitally paralyzed by a bunch of teenagers.
Although LAPSUS$ operations have largely been dormant since the arrests, the cybersecurity community can still benefit greatly by studying this group in more detail. In the coming sections, LAPSUS$ will be used as a case study to demonstrate cyber threat intelligence frameworks.
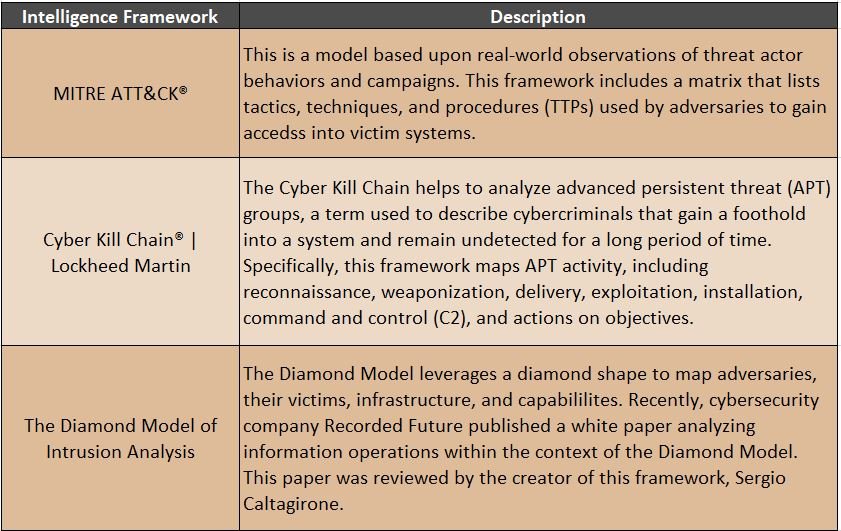
Cyber Threat Intelligence (CTI) Frameworks 101
There are multiple threat intelligence models and frameworks which cybersecurity professionals use in order to examine and analyze events, threat actors, and more. This helps CTI analysts organize information and demonstrate visual patterns in behaviors. Three models or intelligence frameworks that are used frequently are: MITRE ATT&CK®, Lockheed Martin’s Cyber Kill Chain® , and the Diamond Model.
Diamond Model Case Study: LAPSUS$’ Overall Capabilities
As shown in the image below, the Diamond Model was used to conduct a more thorough investigation into LAPSUS$ and the group’s cyber techniques. Starting at the top, we can see that the adversary (LAPSUS$) has developed a number of capabilities using certain infrastructure to connect to and exploit victims. For a more specific example, we can see that LAPSUS$ has stolen credentials via open-source tools such as Mimikatz against victims in several industries. Depicting cyber threat actors in this organized and visualized way can help the community to better understand pattern of behavior.

Diamond Model Case Study: 2022 LAPSUS$ Cyber Attack against Okta
In January 2022, the public security company Okta suffered a cyberattack by LAPSUS$. This incident shook the cybersecurity world, especially given the fact that Okta provides identity management and authentication services to over 15,000 organizations. LAPSUS$ claimed they targeted Okta in order to get access to the company’s customer accounts. In order to further analyze this attack, below is a second Diamond Model with details about this cyberattack.
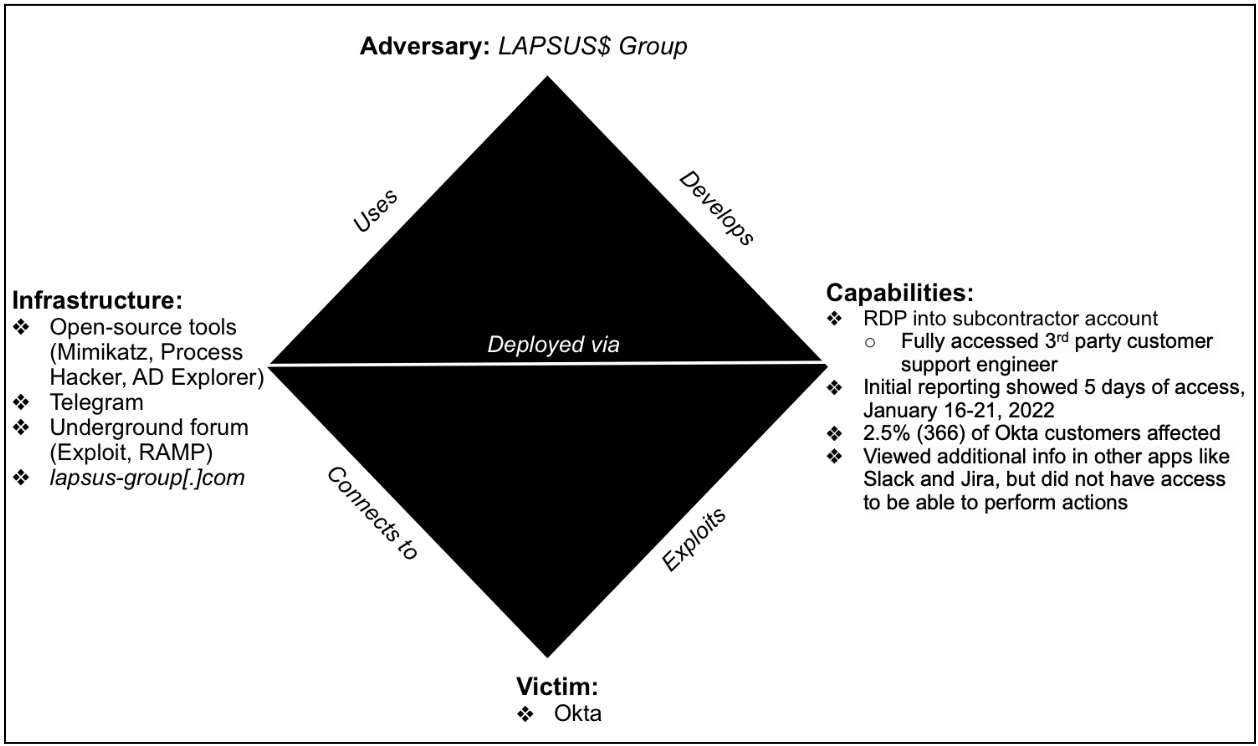
The infrastructure and adversary sections match that of the first diamond model. However, this second diamond model lists LAPSUS$’ specific capabilities used during the attack against Okta. The breach occurred through remote desktop protocol (RDP) into Sitel, a subcontractor of Okta. This allowed hackers to view and access Okta’s data, as shown in the screenshots of the company’s systems that were released by the group’s members. Although Okta’s investigations later showed that the attack was not as nearly as damaging as initially reported, LAPSUS$’ actions demonstrate the prevalence of cyber threats against large organizations.
Conclusion

So why should the industry care about these intelligence frameworks (MITRE ATT&CK, Diamond Model, Lockheed Martin Kill Chain, etc.)? These models allow threat intelligence analysts to take complicated concepts, make assessments, and present findings to the cybersecurity community. Threat intelligence helps the intelligence and cybersecurity professionals as well as non-industry partners to better understand the landscape and access actionable data. Demonstrating common patterns in behaviors in a group such as LAPSUS$ can lead to the advent of better network defenses against not only this particular group but additional hacker groups. Even though LAPSUS$ is not considered to be a refined group, they were able to achieve access and gain ill-begotten fruits from their haphazard labors.
At this time, it is unknown if there are any connections between LAPSUS$ and newer extortion groups. However, there is already a novel extortion group RansomHouse, which is exhibiting TTPs similar to LAPSUS$. Specifically, RansomHouse exploits existing vulnerabilities to gain access to victim networks and exfiltrate sensitive data. Despite its name, RansomHouse does not appear to use ransomware nor does the group encrypt the exfiltrated data.
Whether organizations are being victimized by LAPSUS$, RansomHouse, or another hacking group, the field of cyber threat intelligence has never been more critical in the industry. If you are interested in learning more about cyber threat intelligence, consider reviewing either these resources on Wakelet or this list of terms. We wish to encourage you in your learning journey!
 Meghan Jacquot is a Cyber Threat Intelligence Analyst and is a curious lifelong learner with a commitment to sharing what she has learned. She is passionate about helping others, speaking at conferences to increase cyber awareness, and is particularly interested in cloud security, threat intelligence, and the ethical use of data. She is happy to connect with others on LinkedIn, Twitter (@CarpeDiemT3ch), and on her YouTube channel (CarpeDiemT3ch).
Meghan Jacquot is a Cyber Threat Intelligence Analyst and is a curious lifelong learner with a commitment to sharing what she has learned. She is passionate about helping others, speaking at conferences to increase cyber awareness, and is particularly interested in cloud security, threat intelligence, and the ethical use of data. She is happy to connect with others on LinkedIn, Twitter (@CarpeDiemT3ch), and on her YouTube channel (CarpeDiemT3ch).
 Kate Esprit is a Cyber Threat Intelligence Analyst at MITRE and the Founder of Phishing for Answers.
Kate Esprit is a Cyber Threat Intelligence Analyst at MITRE and the Founder of Phishing for Answers.