Written by: Prajakta Jagdale | Director, Offensive Security | Palo Alto Networks
This will be the first of many posts covering topics across data analysis, data science, data visualization, and machine learning as they pertain to cybersecurity. While it likely will be considered an offense to not talk about Generative AI or language models or ChatGPT, we are going to keep it light for this one.
Let’s begin today with Data Visualization. Data Scientists and Analysts rely prominently on data plots and data visualization to derive numerous insights. Data visualization is also a wonderful storytelling tool. Below are 5 beautiful examples of the meaningful applications of data visualization for cybersecurity.
THE LANDSCAPE
Probably one of the most viewed cybersecurity data plots is developed by Information is Beautiful. There can be no starker picture of the evergrowing cybersecurity threat landscape we are facing.
IT’S ALIVE!
If that wasn’t scary enough, live trackers like the one by Kaspersky emphasize that the attackers never rest. While we enjoy living, breathing entities, rarely do we want to see this in the context of threat activity.

BEAUTIFUL, BUT DEADLY!
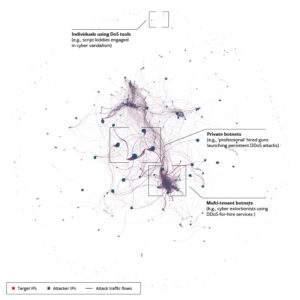
Oldie but goodie, Imperva’s visualization of botnets through the lens of social graphs is not just pretty, but also highly insightful. This a great example of the effectiveness of exploratory overview.
STATS FOR GEEKS
The annual Verizon Data Breach Investigations Reports (DBIR) are some most revered publications across the cybersecurity industry. The DBIR project pioneered the data-focused approach to presenting the state of cybersecurity. The emphasis on data integrity and clever analyses performed over the data makes the reports supremely insightful and a joy to read. Check out the 2022 report here.
Akamai, who partnered with the DBIR project on the 2021 report delved further into various data analysis techniques.
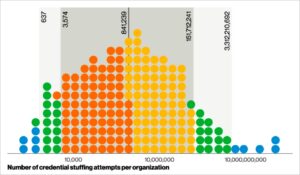
IT’S AN ECOSYSTEM
And lastly, something a bit different. Whether you are a CyberSecurity career aspirant or an experienced professional, we all sometimes could use a reminder of the operational complexity behind the mission of securing an organization. The cybersecurity ecosystem map by Strategy of Cybersecurity does a commendable job of painting the picture.
If you are wondering how to start on a machine learning journey to bolster your cybersecurity portfolio, consider delving into data visualization as your stepping stone.