By: Kaur Ramandeep
Cloud Computing
The evolution of cloud computing has been driven by the need for more efficient, scalable, and cost-effective ways to deliver computing resources. cloud computing has become an integral part of IT infrastructure for businesses of all sizes, providing on-demand access to a wide range of services and resources.
Cloud computing is a technology that enables, on-demand access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) over the internet. Instead of owning and maintaining physical hardware and infrastructure, users can leverage cloud computing services provided by third-party providers
Cloud Migration
There is a large shift happening right now, in which companies continue to move workloads from their data centres into the cloud. Cloud migration is a software strategy that involves encapsulating legacy applications in containers and deploying them in a cloud computing environment.
Cloud computing is commonly categorized into service models and deployment models:
Service Models
Infrastructure as a Service (IaaS):
Provides virtualized computing resources over the internet. Users can rent virtual machines, storage, and networking components.
Platform as a Service (PaaS):
Offers a platform that includes tools and services for application development, testing, and deployment. Users can focus on building applications without managing the underlying infrastructure.
Software as a Service (SaaS):
Delivers software applications over the internet on a subscription basis. Users access the software through a web browser without worrying about installation or maintenance.
Deployment Models
Public Cloud:
Resources are owned and operated by a third-party cloud service provider and are made available to the general public.
Examples – AWS, Azure, and Google Cloud Platform.
Private Cloud:
Resources are used exclusively by a single organization. The infrastructure can be managed by the organization or a third party and can be located on-premises or off-site.
Hybrid Cloud:
Combines public and private cloud models to allow data and applications to be shared between them. This provides greater flexibility and optimization of existing infrastructure.
Unfortunately, every rapidly growing industry attracts not only enthusiastic entrepreneurs but also malicious players, whose goal is to detect and take advantage of any security holes that would be unable to defend against various attacks.
Examples of common attack scenarios
1.DDoS attack occurs when a web application is overloaded with a high volume of traffic. But use of DDoS protection services, like AWS Shield can mitigate such attacks.
AWS Shield is a managed Distributed Denial of Service (DDoS) protection service offered by Amazon Web Services (AWS). It uses machine learning algorithms to analyse incoming traffic and identify patterns indicative of a DDoS attack.
2.Data Breach involves exploiting vulnerabilities to access and exfiltrate sensitive data. But regularly updating software, encrypting sensitive data, and monitoring for unusual activity and building a good incident response.
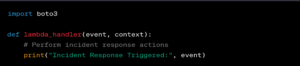
3. Man-in-the-Middle (MitM) Attack occurs when communication between two parties is intercepted for malicious intent. The use encryption (SSL/TLS) and implementing the secure communication protocols can help. Without encryption, data transmitted over the network may be intercepted.
Below code is an example of encrypting S3 Objects with AWS SDK for Python-Boto3
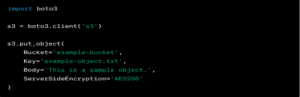
4. Brute Force Attack – A brute force attack is a hacking method that uses trial and error to crack passwords, login credentials, and encryption keys. It is a simple yet reliable tactic for gaining unauthorized access to individual accounts and organizations’ systems and networks.
AWS CloudWatch Alarms can provide the logging and monitoring services where repeated login attempts might go unnoticed.
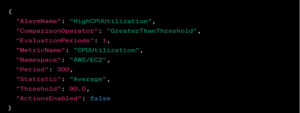
Security in cloud computing involves implementing measures to protect data, applications, and infrastructure in a cloud environment from potential threats.
Here are some best practices in key areas of cloud configurations in AWS, Azure, GCP associated with securing cloud environments.
AWS
Identity and Access Management (IAM):
- Use the principle of least privilege when assigning permissions to users, roles, and groups.
- Regularly review and audit IAM policies to ensure they align with business requirements.
- Enable multi-factor authentication (MFA) for enhanced user authentication.
Example AWS IAM Policy
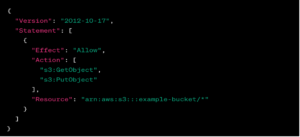
If IAM policies are not properly configured, an attacker might gain access to sensitive resources.
VPC (Virtual Private Cloud) Configuration:
- Utilize separate subnets for public and private resources.
Example Code (AWS CloudFormation)
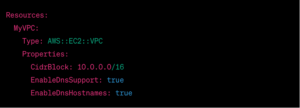
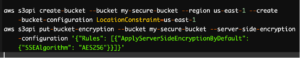
S3 Bucket Security:
- Regularly audit and review access controls for S3 buckets.
- Enable versioning and logging to track changes and access to objects.
- Consider using S3 bucket policies to control access at the bucket level.
- Enforce server-side encryption for S3 buckets.
Example Code (AWS CLI)
Azure
Azure Role-Based Access Control (RBAC):
- Assign the principle of least privilege using Azure RBAC.
Example Code (Azure PowerShell)
![]()
Blob Storage Security:
- Enable Blob storage encryption
Example Code (Azure PowerShell):
![]()
Azure Virtual Network:
- Implement network security groups (NSGs) for access control.
Example Code (Azure Resource Manager Template):
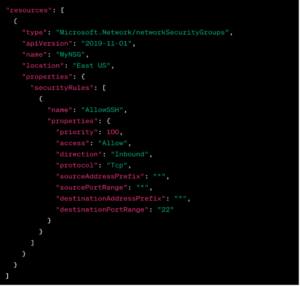
Conclusion
Securing cloud configurations is paramount in safeguarding digital assets and maintaining a resilient cybersecurity posture. A focus on continuous monitoring, compliance checks, and proactive incident response planning to address the dynamic nature of cyber threats can help survive one.
Implementing the principles of least privilege, encryption, identity and access management, and network security best practices not only protects the cloud environment against potential vulnerabilities but also contributes to a culture of security awareness and responsiveness within the organization.
As cloud computing continues to evolve, a commitment to staying ahead of emerging security challenges and adapting configurations accordingly is imperative for maintaining a resilient and secure digital presence.